When I tell people I’m traveling around the world studying hackers and free software activism, some of the most common reactions I get are along the lines of, “Isn’t that illegal?”, “Make sure they don’t steal your credit card number,” or “I can’t believe they’d let you meet with them.”
Reactions like these betray a fundamental and all-too-common misunderstanding of who hackers are and what they do. At its most basic, a “hacker” is one who hacks. The word ‘hack’ originated at MIT in the 1960s and 70s, where it meant something like “messing around”. One of the earliest applications of the term was for students who explored locked parts of buildings or steam tunnels under the campus. This was known as “tunnel hacking”. Later, the word came to refer to elaborate and intricately planned pranks orchestrated by MIT students. The Jargon File (an invaluable repository of hacker culture) lists examples such as putting a police cruiser on the roof of a building, or inflating a huge ‘MIT’ balloon at the 50 yard line during the Harvard-Yale football game.
From this early use, the term spread to the MIT AI lab, which was one of the major hotspots of early computer and software development, and one of the birthplaces of computer hacking. It was there that “hacker” took on its current meaning. The exact definition depends on who you ask, the jargon file lists eight separate meanings, but others would claim fewer, MIT hacker Phil Agre is quoted as claiming that, “The word hack doesn’t really have 69 different meanings. In fact, hack has only one meaning, an extremely subtle and profound one which defies articulation.”
To me, the key thing that makes something a good ‘hack’ (and its perpetrator by extension, a ‘hacker’) is that it involves cleverness and elegance (either in the form of clean efficiency, or intentionally absurdest inefficiency). Brian Harvey of UC Berkley (another important site in the history of software) argues that what makes a hacker, is at its core, an aesthetic judgment, and I’m inclined to agree. One of the best (although not necessarily most succinct) expositions of what it means to be a hacker is given by Eric S. Raymond. He lists the central tenants of hacker philosophy as:
- The world is full of fascinating problems waiting to be solved.
- No problem should ever have to be solved twice.
- Boredom and drudgery are evil.
- Freedom is good.
- Attitude is no substitute for competence.
There are many people who will claim that, “hacker” refers unambiguously to noble, ethical, hobbyist-tinkerers. They argue for the use of “cracker” to refer to malicious computer criminals. Leaving aside the fact that cracker already has a much better-established slang meaning, in my opinion, the people who argue the loudest in favor of “cracker” tend to be IT nerds who want the cred that comes with the label “hacker”, but don’t want to accept the moral ambiguity and anti-authoritarian connotations that come along with it. Just because you write code for a living, it doesn’t make you a hacker. In fact, it may even be a mark against your hacker-dom. A true hacker doesn’t write code to make a living, s/he codes to solve an interesting problem in an elegant way.
The truth is that “hacker,” encompasses both ethical coders and malicious criminals. Some criminals have been very inventive and creative in their efforts to compromise systems. By the same token, most computer criminals are not all that clever. It is a simple matter to download ready-made tools which can be used to, crack wifi encryption, or orchestrate a DoS attack, for example. These people are not hackers, they are script kiddies.
My preferred nomenclature is the one which uses “Black Hat,” or “White Hat Hacker” for cases where it is necessary to distinguish and separate hackers who engage in criminal behavior from those who do not. I feel that this terminology preserves the full range of meaning for “hacker” and doesn’t resort to silly invented (as opposed to organically developed) terms like “cracker” to draw the distinction.
If this all seems a bit complicated, it’s because it is. To help clarify things, I made a little Venn Diagram:

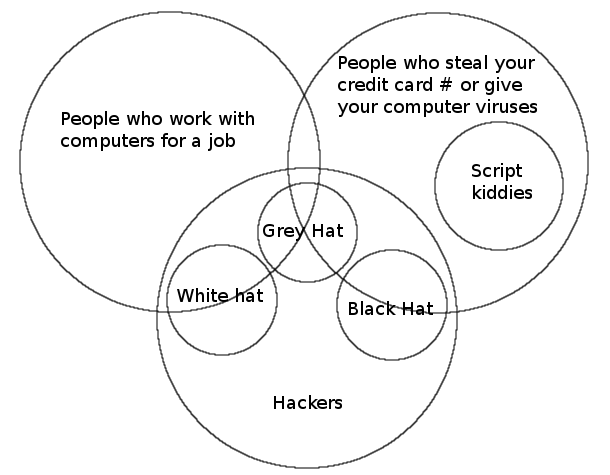
Very interesting, but how do you know what type of hacker you are dealing with until the hack is complete?
I don’t know, to me, hacker has little to do with application, and I think this is a new modern obsession founded by those in the computer security industry who seemed to have hijacked the term due to media attention on their activities and the potential impact on society of them. I believe it it a fundamentally flawed perspective because it focuses solely on modern advances in *PC* technology and communications that did not even exist when the term began being used.
I also don’t believe that the hacker mentality is very philosophical. In fact, this might be the defining trait of a hacker versus other intellectuals in their field. Hackers just fixate on solving difficult, non-linear problems with unclear “solutions”. There is a very point A-B perspective, no papers over analyzing why that technique worked or justifying why they chose a hash table over a red-black tree for their design.
Classification also seems to assume that hackers care at all about the ethics of what they do, which does not seem to be the case much of the time. It seems to me more like their ethics merely reduce to the context of what interests them or what environment they are in, as much as they may profess differently. Perhaps this is not much unlike any other intellectual movement. For example, those who were interested in an accurate study of astronomy once had to exhibit criminal behavior to achieve it. Now they seem like the nice if boring guy next door: all context, no ethics.
The hacker philosophy is a good summary but is perhaps intentionally vague, and also tries to hijack the term for directly supporting the FSF philosophy. For example, tenants 3 and 4 can either be selfish, humanist, or somewhere between. Tenant 2 has always struck me as confusing being on of the things many hackers love to do when they learn a new technology or technique is implement “Yet Another %s” with it. Perhaps he just used “have” strictly.
Now a more interesting analysis would be not what a hacker is but what he isn’t. Many other problem-solvers and innovators seem to have characteristics and philosophies that seem to hopelessly clash with those of the hacker, yet they are clearly, to me at least, not hackers.